SOS
Development
I implemented the project together with my fellow student Andreas Kägi for the ?Advanced Operating Systems? course at ETH during the spring semester 2008.
Detailed Description
SOS is, as its name indicates, a simple operating system. It is based on:
- The L4 Pistachio microkernel developed by University of Karlsruhe
- The NSLU2 Linksys network storage controller. There are various resources online providing detailed information on this piece of hardware. It features a 133 Mhz 32bit ARM CPU based on the Intel XScale processor and 32 MiB RAM. Additionally it has a debug serial to USB port and IXP420 network ports.
SOS basically implements all the details making up an operating system. The features range from the basic paging and page swapping subsystems to a unified application programming interface. During the development in order to keep a clean software architecture care was taken to keep the original idea of a microkernel even though the resulting performance was not as expected. Main benefits from the microkernel architecture are a simple kernel level core and a set of advanced user space services. These services already profit from higher level abstractions like the paging subsystem which makes development a lot easier and less error prone. A detailed overview over the main software architecture follows.
Technical Details
- Additional Developers: Andreas Kägi
- Programming Language: C
- Development Environment: Eclipse CDT
- Project Size: 183 files, 26'615 code lines, 8'869 comment lines, 8'743 blank lines, 1.54 MiB code
- Technology used: Pistachio L4 Microkernel, Intel IXP420 device driver
Feature List
- Pure microkernel design
- A memory manager
- A pager based on the memory manager
- A unified system call interface (API)
- A file system
- On demand page swapping
- A timer driver
- Process and thread abstractions and management
- ELF loading
- Drivers loaded using the file system
Hardware
Software Architecture
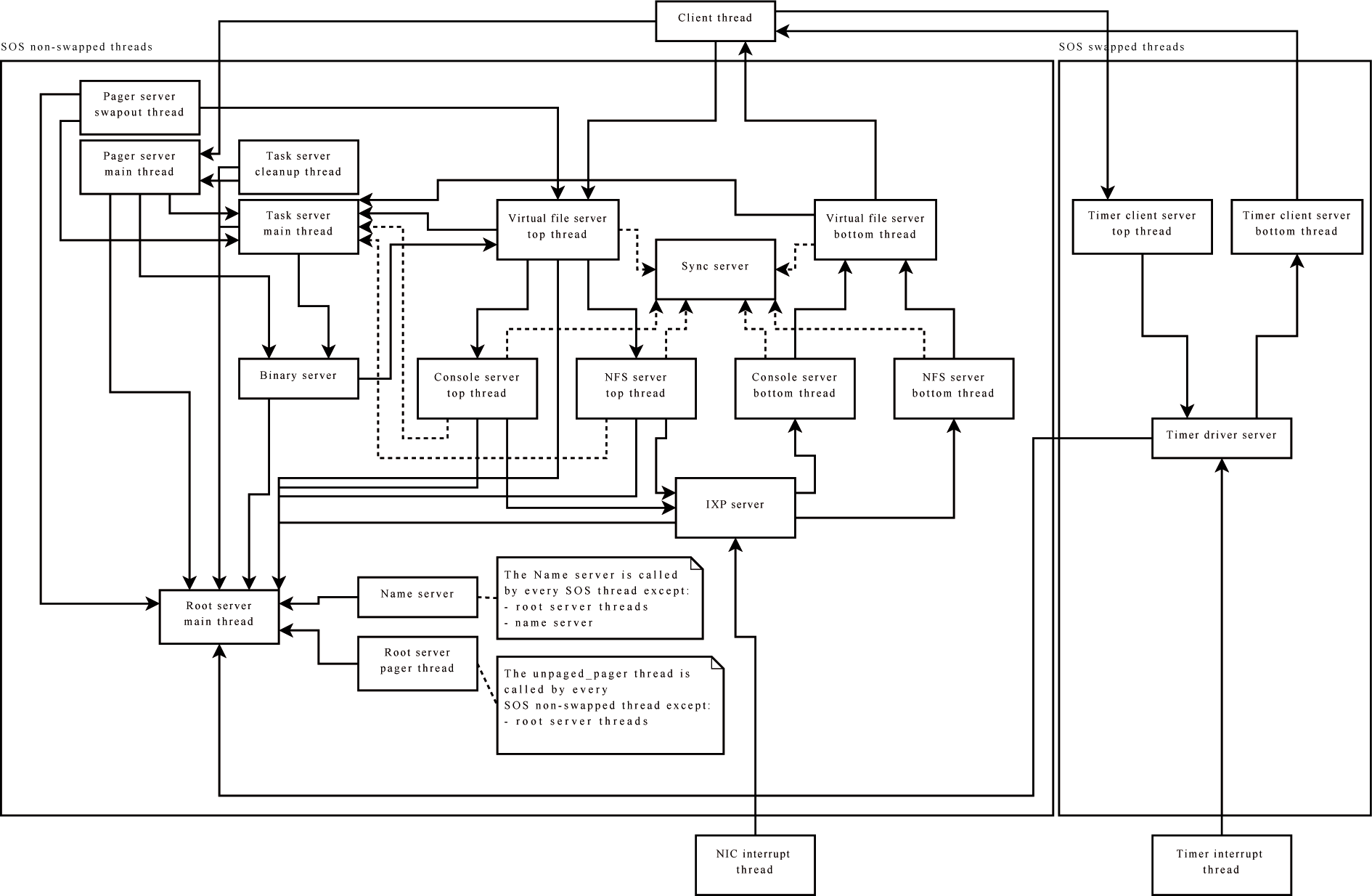
The following picture should give a rough overview of how the operating system is structured internally. As can be seen it consists of pieces of independent servers providing the operating system functionality to client processes. For a more detailed comment please look at the documentation provided with the additional material.
Challenges
The main challenge in SOS was the time pressure that we had. Nearly every week was a new milestone with new functionality. And since we had to work with a given codebase that we did not know beforehand this led to a large piece of code which was full of dependencies and other software engineering nightmares. Some teams attending the course kept the code base until the end of the course and spent every week more time with debugging. We on the other hand tried to solve the problem with a completely new architecture once we knew our code base. This led to an enormous amount of work during the time we were refactoring because we still had to implement new features. We also missed one milestone and lost points due to that work. But in the end I think it was worth the effort and paid off with bonus points, less time spent to debug and less time pressure compared to the other teams.
Code Sample
The code sample shows the main function of the process handling the system calls to load executable binary files.
//-----------------------------------------------------------------------------------------------------------
static void sos_binaryserver_handle_message(
L4_ThreadId_t tid,
L4_MsgTag_t* tag,
L4_Msg_t* msg,
int* send) {
sos_dbg_trace(SOS_TRACE_BINARYSERVER, "got msg from 0x%08lx, (%d %p)\n",
tid.raw, (int) TAG_SYSLAB(*tag),
(void *) L4_MsgWord(msg, 0));
switch (TAG_SYSLAB(*tag)) {
case SOS_SYSCALL_BINARYSERVER_WAIT_UNTIL_READY:
case SOS_SYSCALL_BINARYSERVER_MOVE_TO_L4_ADDR_SPACE:
case SOS_SYSCALL_BINARYSERVER_FREE_BINARY: {
sos_binaryserver_handle_small_syscall(tid, tag, msg, send);
break;
}
case SOS_SYSCALL_BINARYSERVER_LOAD_BINARY: {
sos_binaryserver_handle_large_syscall(tid, tag, msg, send);
break;
}
default: {
sos_dbg_trace(SOS_TRACE_ERRORS,
"************** unknown system call from 0x%08lx with label: %d!\n",
tid.raw, TAG_SYSLAB(*tag)
);
// Unknown system call, so we don't want to reply to this thread
//sos_print_l4memory(&msg, L4_UntypedWords(tag) * sizeof(uint32_t));
*send = 0;
break;
}
}
}
Additional Material / Downloads
Related Links